Today, I found some weird permission fault/bugs of SharePoint 2013/ Office 365.
We have one portal site collection, which contains sub-sites like HR, IT etc.
Where all users have full control on Root site and HR sub-site having unique permissions. Only HR Group will access HR sub-site.
For example, I (Hemant) does not have any permission on HR site. But having full permissions on Root site.
Created one sample SharePoint Designer Workflow. Which contains App Step activity, which requires you to wrap any actions in your workflow that require elevated permissions on root level site.
Activation of this feature is necessary for the App Step to become available for use in SharePoint Designer 2013:
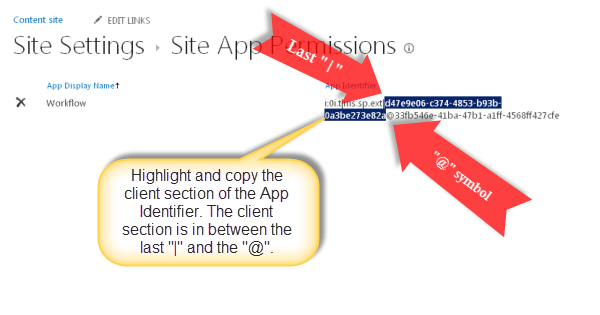
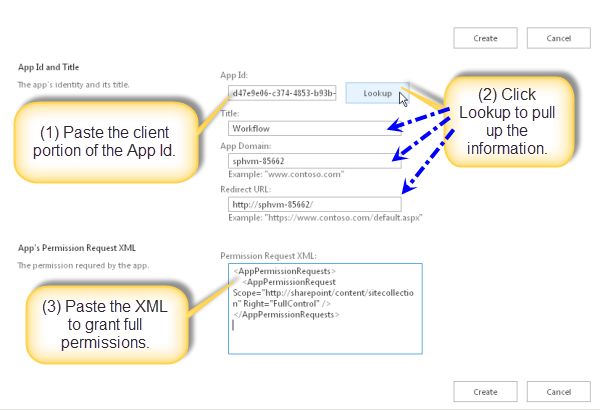
https://rootsite/sites/HR/_layouts/ 15/appinv.aspx
Now we will start hacking!!!
Once the above steps are configured. Then any users who has the full controls on root site can configure SPD workflow and by using App Step activity in SPD workflow, user can perform read/write/delete operations on sub-site even if user does not have any access on sub-site.
For example, Hemant doesn’t have access on HR sub-site and he has full control on root web. So he can create SPD workflow and by using App Step activity in workflow, he is able to read data from sub-site and even he is able to delete entire sub site by using HTTP web service call in App Step activity.
Now we will move to SharePoint designer to configure the workflow on root site list with app step which will read sub-site’s title by using HTTP web service call.
I know App Step provides facility to run SPD activity under Service Account user. But by performing the above operations, you can see that user who does not have permission on sub-site, can perform any operations on the sub-site by creating the SPD workflow on the root web once the workflow app identifier is configured.
Should Microsoft SharePoint 2013 have to provide some solution so user with limited permission cannot create workflow with App Step?
Otherwise user who has permission on root web can delete the sub-site by creating workflow once the workflow app identifier is configured.
Also posted the same thread on Microsoft technet to get more feedback: https://social.technet.microsoft.com/Forums/en-US/3382a54d-7fff-4ca3-893a-49f1c2f70d0c/without-permissions-you-can-perform-readwritedelete-operations-on-sharepoint-2013?forum=sharepointcustomization
Find more details on office 365 community: https://community.office365.com/en-us/f/148/t/411719
Please provide your views !!
Thanks,
?width=699?width=600?width=600?width=750?width=750?width=750
Yes, we can disable the SPD for the site. But, I think it’s not a proper approach or solution. Microsoft must provide some security mechanism to restrict workflow creator to performs actions on the content on which workflow creator don’t have a permission while creating workflow using app step activity. In SharePoint 2010, When we use the Impersonation activity, then steps inside impersonation are running under the context of workflow creator. So if workflow creator doesn’t have access then we will get unauthorized error, while in SharePoint 2013, App step activity is using the System Account for impersonation.
Thanks
Disable SPD access to the site. SPD is the issue, not the app model.
Thanks Paul,
I know app step is using the system account to execute the steps inside it and if we don’t use app step, then of course, it will result in unauthorized access.
But, anyone, you can say, by intentionally, user , who has no permission on the List (Unique Permission List), can create workflow on list (Full Permission List) on which user have full permissions and use the app step activity to retrieve/ add/ delete operation to unauthorized list. I have explained the same scenario in above forum.
Here, Unauthorized user can access restricted items (Unique Permission List) using app step activity in SPD workflow. So developer can use the App Step activity to access or even delete the secure items of list/sub sites. So should Microsoft has to provide any security mechanism so that in App Step activity, workflow creator cannot include activity steps for those lists on which workflow creator doesn’t have permission (like performing action on unauthorized list).
This isn’t a bug. By using App Step, you are telling SP to use app-only permissions instead of app+user. If you do so, that is at your own risk. If you want to include the user’s permissions, you need to increase the app principal’s but do not use the App Step in the workflow. If your concern is that a malicious user could create a workflow in SPD using an App Step, then you should disable SPD connections to the site.